Would You Entrust Your Data to These Yokels?
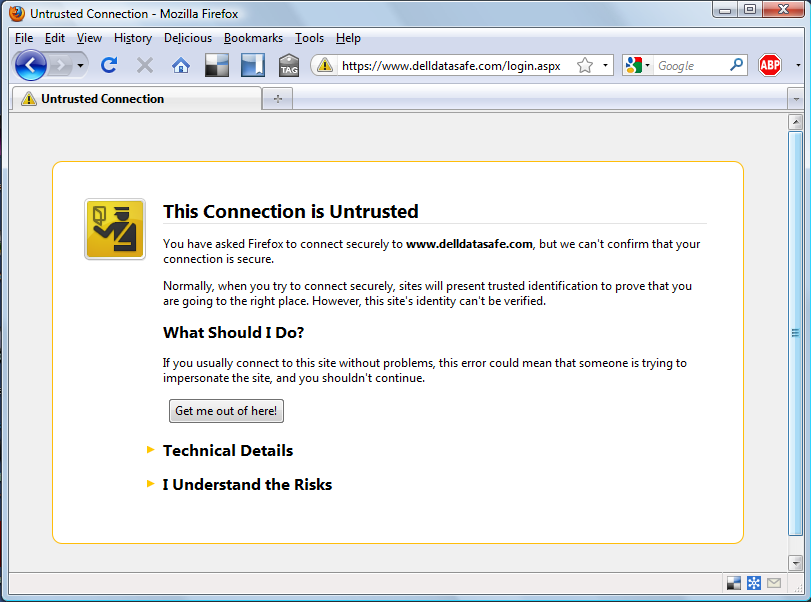
If Dell can’t even manage their public key certificates, how can I trust them to keep my data safe and secure?
Technical Details
www.delldatasafe.com uses an invalid security certificate.
The certificate is not trusted because the issuer certificate is unknown.
(Error code: sec_error_unknown_issuer)

December 31st, 2009 at 9:07 am
Yes, but to be fair, these certificates are a bit of a Ponzy scheme.
December 31st, 2009 at 9:28 am
The cert shows as valid on Firefox 3.5 and Opera 10.x on Windows 7 (the root CA is GTE Cybertrust Global Root).
December 31st, 2009 at 11:19 am
They seem to have fixed the problem. Not sure if that’s coincidence or not. I’ve noticed before that Dell pays a lot closer attention and responds much faster to what people post about them on the Web than they do to their phone support tree.
December 31st, 2009 at 4:27 pm
PKI as currently implemented in browsers is a farce. There are some 400 trusted CAs in Firefox’s tables, and new ones being added all the time. Many of these have expired and some have even been revoked. And it’s an open secret that you can get your certificate signed on less than no evidence at all: basically “Pay me $$$ and I’ll say you are who you say you are.”
When Reuters Health processed credit-card purchases (it no longer does), we self-certified. It’s impossible to say how many people didn’t buy because of that, obviously, but only one person ever complained during the entire couple of years.
December 31st, 2009 at 11:03 pm
What a great find. I wish that I had researched this more when I first saw the post. On my Mac, safari showed a valid cert, but firefox did not. Using the portecle utility to examine the ssl connection, I noticed that the server was sending only one certificate as part of its handshake.
I believe that Sarari (and almost certainly IE but I didn’t test) showed the certificate as valid because they can do more dynamic work to build the certificate chain. The fancy work is to process the certificate AIA extension to fetch the CA for the certificate being evaluated and thereby dynamically build the certificate chain to a trusted root – gte cybertrust. Sadly, I didn’t do a packet capture just then, and the behavior has been updated to support Firefox.
I expect that someone only tested with IE and didn’t catch that other browsers didn’t work. The fix was to have the web server send the intermediate CA certs in the chain, too. This is interesting because I have not seen browsers do the dynamic path building using the AIA extension outside of a lab.
January 1st, 2010 at 8:52 am
Interesting. So maybe it’s a Firefox bug? (which still doesn’t get Dell off the hook for not testing in Firefox)
January 3rd, 2010 at 12:11 am
No, I wouldn’t call this a bug unless firefox advertises this functionality. A quick google search suggests that the functionality is being developed but isn’t in firefox 3.5.
This functionality makes for a cool demo of microsoft technologies with their CA and browser. A good use case is that an enterprise does not have to distribute the CAs through group policies or whatever since its users are all on the corporate standard browser. Usually the disappointment sets in when you realize that the actual corporate standard (ie6) doesn’t support all of the cool functionality (I’m not sure about the AIA feature, though, which may work in ie6) and that a lot of users are trying to ditch the corporate standard by running firefox.
It is not surprising that dell appears to be using a dell-operated CA (almost certainly running microsoft’s CA) to issue this ssl server cert.
January 13th, 2010 at 11:47 am
And what about this jokers : http://dbj.org/dbj/?p=92
January 19th, 2010 at 8:42 am
Sun’s Kenai site has been promising future Hudson services for a while now.
February 11th, 2010 at 12:56 pm
Haha,
who cares??
i am happy aslong as there is a cryptation there.
the cert is just bullshit so companys can steal my money.
if they whant to hack the oregin there is not really a probelm for the hacker.